This page covers Virtualization, and Library routines.

Arrow key down to the area shown. When you hit <Select> at this point, you will bring up the following sub page:
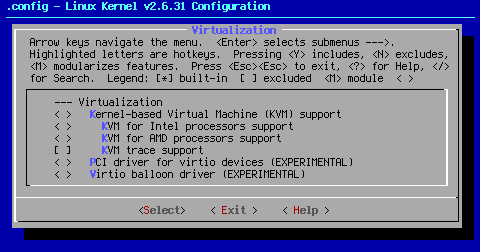
KVM (Kernel-based Virtual Machine) is a way to use your Linux install to run other operating systems like Windows and other Linux distributions. As such, it is clearly not a thing needed to get a computer up and running Linux alone. Since KVM is not a strict need to get your Linux kernel up and running, it follows I don't support it. Click here for more information on KVM.
--- Virtualization
< > Kernel-based Virtual Machine (KVM) support
This option provides access to the system hardware through a character device named /dev/kvm.
< > KVM for Intel processors support
This option provides support for KVM on Intel processors equipped with the VT (Virtualization Technology) extensions.
< > KVM for AMD processors support
This option provides support for KVM on AMD processors equipped with the AMD-V SVM (Secure Virtual Machine) extensions.
[ ] KVM trace support
This option allows reading a trace of kvm-related events through relayfs.
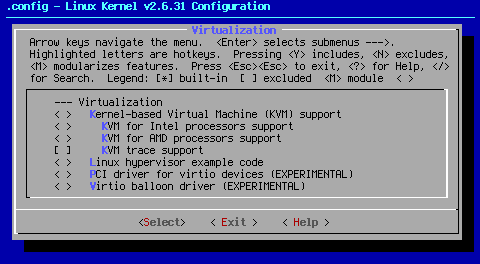
x86 < > Linux hypervisor example code
This option allows you to run multiple instances of the same x86 Linux kernel, using the "lguest" command.
< > PCI driver for virtio devices (EXPERIMENTAL)
Virtio is a Linux standard for network and disk device drivers where just the guest's device driver "knows" it is running in a virtual environment, and cooperates with the hypervisor.
< > Virtio balloon driver (EXPERIMENTAL)
This driver supports increasing and decreasing the amount of memory within a KVM guest.
Arrow key down to the area shown. When you hit <Select> at this point, you will bring up the following sub page:
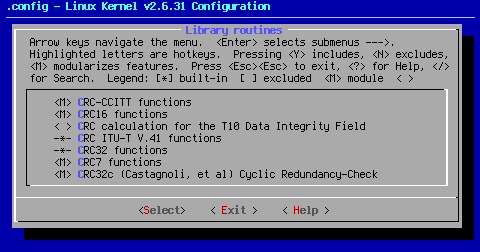
Cyclic redundancy checking (CRC) is an insecure hash function designed to detect accidental changes to raw computer data. It is commonly used in digital networks and storage devices such as hard disk drives. These options allow for CRC outside the kernel which can be used by userspace programs and hardware devices. < Help > recommends these options are set as modules.
The entries below describe which devices are covered by which CRC functions. You can turn off options that do not pertain to your system if necessary. When these options are used, it is recommended by < Help > that they be set as modules. Defaults are shown.
<M> CRC-CCITT functions
XMODEM, Bluetooth.
<M> CRC16 functions
Standard block devices.
< > CRC calculation for the T10 Data Integrity Field
SCSI block devices with T10.
-*- CRC ITU-T V.41 functions
Modems.
-*- CRC32 functions
Ethernet devices, POSIX checksums.
<M> CRC7 functions
Telecom.
<M> CRC32c (Castagnoli, et al) Cyclic Redundancy-Check
iSCSI and SCTP.
This is the end of page 13.
Cheers,
Pappy